IP Privacy Detection Extended Database Developer Resource
Privacy Detection extended database reveals IP addresses linked to VPNs, Tor, proxies, relays, and hosting services. The database helps users to understand how we detect anonymous IP addresses so that they can use this information to build personalized cybersecurity policies.
Database Schema
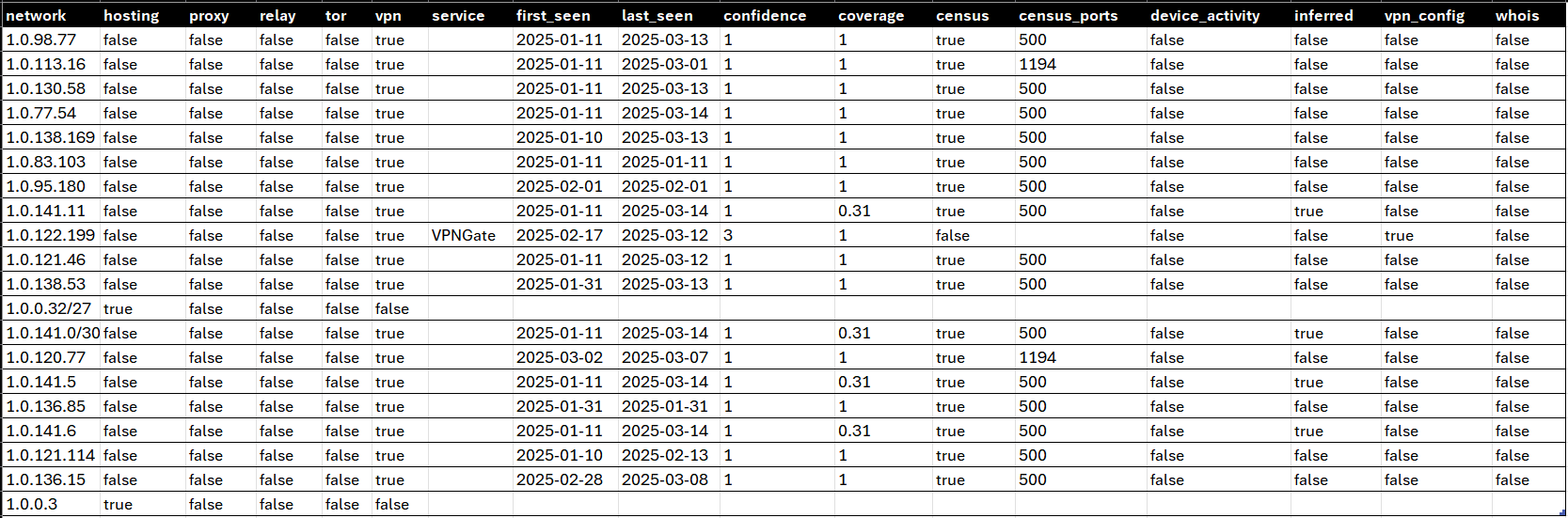
The Privacy Detection extended database contains the following fields:
| Field Name | Example | Data Type | Descrption |
|---|---|---|---|
| network | 45.129.35.234 | TEXT | CIDR/IP Range or single IP address block |
| hosting | true | BOOLEAN | Indicates a hosting/cloud service/data center IP address |
| proxy | false | BOOLEAN | Indicates a open web proxy IP address |
| relay | false | BOOLEAN | Indicates location preserving anonymous relay service |
| tor | false | BOOLEAN | Indicates a TOR (The Onion Router) exit node IP address |
| vpn | true | BOOLEAN | Indicates Virtual Private Network (VPN) service exit node IP address |
| service | NordVPN | TEXT | Name of the privacy service provider includes VPN, Proxy and Relay service providers names |
| first_seen | 2024-10-31 | DATE | Date when the activity on an anonymous IP address was first observed: Date in YYYY-MM-DD format, ISO-8601. Within the 3-month lookback period. |
| last_seen | 2025-01-03 | DATE | Date when the activity on an anonymous IP address was last/recently observed: Date in YYYY-MM-DD format, ISO-8601. |
| confidence | 3 | INTEGER | The level (from 1 to 3) of confidence attributed to the best source associated with this range |
| coverage | 1.0 | FLOAT | For inferred ranges (see inferred flag), represents the proportion of the range (in IP count) that we saw direct evidence of VPN activity on; the remaining percentage of the range (1 - coverage) is composed of IPs we did not directly observe. For IPs/ranges we've fully directly observed VPN evidence on, this value is 1.0. |
| census | false | BOOLEAN | Ranges where we've observed VPN software/ports on; we run scans on ports and protocols commonly associated with VPN software. Ranges with the census flag are those where these scans obtained positive results |
| census_ports | INTEGER | The ports we've gotten positive results for when running our VPN detection census | |
| device_activity | false | BOOLEAN | Ranges on which we've observed device activity compatible with VPN usage (outside of known infrastructure area; simultaneous use around a large area; pingable and/or associated with hosting providers) |
| inferred | false | BOOLEAN | Whether the range associated with the record is the result of direct observation or inference based on neighboring IPs |
| vpn_config | true | BOOLEAN | Ranges where we confirmed VPN activity by directly running VPN software from almost 200 different providers and collecting exit IPs |
| whois | false | BOOLEAN | Ranges where we've observed VPN software/ports on AND have a WHOIS association with either VPNs in general or specific VPN providers. e.g. if our ipsec scan returned a positive result for an IP and its WHOIS record indicates that it is owned by a VPN provider, this flag will be true. |
Confidence intervals defined:
| Confidence Level | Description |
|---|---|
| 3 | Direct observation of commercial use (vpn_config) |
| 2 | Direct observation of VPN software running on the range (census) + registrar information associated with VPNs or specific providers OR highly convincing device activity (large spread of devices on pingable networks that are not associated with carrier traffic and known to be associated with hosting providers) |
| 1 | Direct observation of VPN software running on the range (census) without known association to specific providers or VPNs in general OR device data that is suspicious but not associated with hosting ranges |
Sample Databases
- Privacy Detection Extended Database Sample — CSV
- Privacy Detection Extended Database Sample — JSON
- Privacy Detection Extended Database Sample — MMDB
Filename references:
| File Format | Filename / Slug | Terminal Command |
|---|---|---|
| CSV | ipinfo_privacy_extended.csv.gz | curl -L https://ipinfo.io/data/ipinfo_privacy_extended.csv.gz?token=$TOKEN -o ipinfo_privacy_extended.csv.gz |
| MMDB | ipinfo_privacy_extended.mmdb | curl -L https://ipinfo.io/data/ipinfo_privacy_extended.mmdb?token=$TOKEN -o ipinfo_privacy_extended.mmdb |
| JSON | ipinfo_privacy_extended.json.gz | curl -L https://ipinfo.io/data/ipinfo_privacy_extended.json.gz?token=$TOKEN -o ipinfo_privacy_extended.json.gz |
| Parquet | ipinfo_privacy_extended.parquet | curl -L https://ipinfo.io/data/ipinfo_privacy_extended.parquet?token=$TOKEN -o ipinfo_privacy_extended.parquet |
Links
- Available on Snowflake Marketplace
- IPinfo Sample Database Repo — GitHub